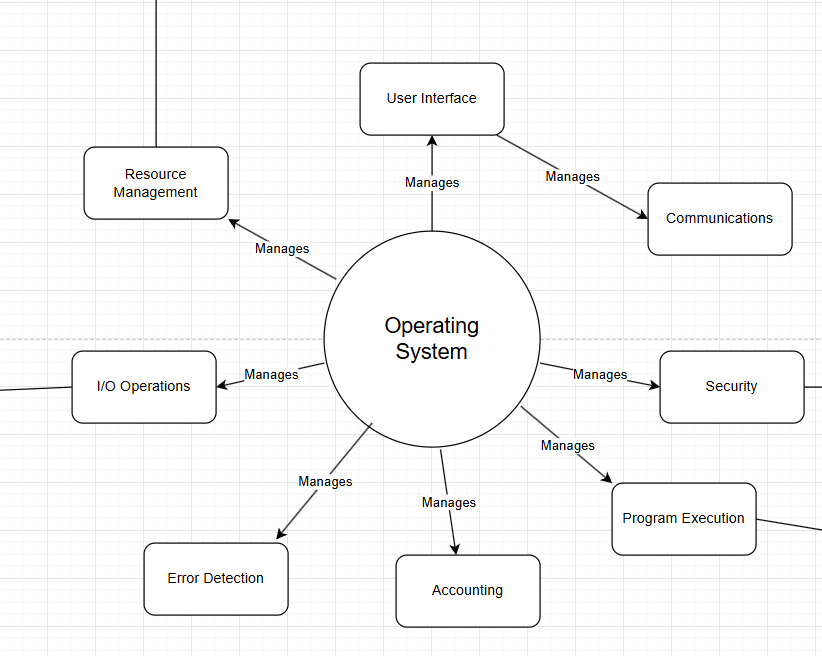
Contemporary operating systems use a variety of features, such as memory management, I/O operations, error detection, accounting, program execution, security, and user interface. This allows for a more complex but user-friendly system. It also allows for multitasking, something vital in the modern day-to-day. It can be represented in a multitude of ways, but I have chosen to show it in this way.
Tec101 Blog
Blog about information technology
Search This Blog
Tuesday, March 4, 2025
Nicholas Barnes CYB304 Final
Tuesday, June 20, 2023
Final
Operating Systems
Information technology without operating systems would be like a human body without a brain. It just would not be able to function. Sure, you can have all the required parts lined up, but without the brain to function, it will be lifeless. That is exactly what an operating system is to a computer, which means it is inherently important to information technology as a whole. It embodies the idea of information technology, the ability to choose and customize while having hard-set rules to follow. Only operating systems have as much power over whether or not you can do something other than maybe the power to the computer.
In the earliest times of computers, they actually did not have operating systems. Each part had to be connected manually, making it tremendously slower than modern computers. It could only run one job at a time and would not be improved for about a decade. The big transition was in the 1960s when it was enhanced to the point that computers could run multiple jobs at once with the help of an input/output control system (IOCS). These were the rudimentary operating systems.
During these early times, a major flaw was discovered. “As more and more data started to be transmitted through the communication lines, they became more and more vulnerable to interception and unauthorized access.” (Moumina, 2001). This required the users to create a strategy to combat potential security threats. “Encryption received much attention – it became necessary to encode proprietary or private data so that even if the data were compromised, it was not of any value to anyone other than the intended receivers.” (Moumina, 2001). This led to the creation of a stronger, more secure operating system.
The hardware that is required to have an operating system is the random access memory (RAM). It is run alongside any programs that are running and is used to keep the system going. It will be automatically booted up whenever the computer is run, as long as it is downloaded there. It functions much like any computer program but with a much larger scope of control on your computer.
The coding required to create an operating system is generally quite complex. It has to be a high-level programming language such as C, C+, or Python to be able to create such a complex program. It will also require an assembly language used to communicate between all the processes throughout the computer. It can end up being hundreds, if not thousands, of lines of code.
The relationship between an operating system and application software has many similarities but also many differences. Application software is software designed to do specific tasks. It generally only performs a single task, unlike an operating system that completes a multitude. Because of this, though, they can be highly specialized to complete that specific goal. If you need something particular done, application software is the way to go over an operating system.
A significant connection that the operating system has is to the database of the computer. A database manager is used to access and sort through the computer’s database. It is described as “a computer program, or a set of computer programs, that provide basic database management functionalities including creation and maintenance of databases. Database managers have several capabilities, including the ability to back up and restore, attach and detach, create, clone, delete and rename the databases.” (Rouse,2011). Both are major functions of a computer and often communicate with each other depending on how the user is trying to access their files.
References
Moumina, A. (2001). History of operating systems.
Rouse, M. (2011). Database Manager.
Friday, June 16, 2023
Post 6
In modern times, technology is the fastest-growing market in the entire world. We use it for anything and everything, and we are constantly personalizing it as we go. We input our data on websites and applications, or it is stored for banks, stores, or even the government. Somehow your data is going to be stored on the internet. With this, your data can become vulnerable to hackers and thieves looking to take advantage of your data. Because of this, we need information security. “Weak data security can lead to key information being lost or stolen, create a poor experience for customers and reputational harm. Data breaches, fraud, and cyber-security attacks are all becoming more common as people become more reliant on technology.” (Dataguard, 2022).
One of the ways that your information can be attacked is through ping commands. Using ping commands, attackers bombard a device or system with ICMP request (ping) commands through the web, making it difficult to access your device. This can be called a Ping Flood and is considered a form of DDoS attack.
Another way that attackers can access your data is through phishing. The Oxford Dictionary defines phishing as “the fraudulent practice of sending emails or other messages purporting to be from reputable companies in order to induce individuals to reveal personal information, such as passwords and credit card numbers.” Nowadays, these emails and phone calls are commonplace. Unfortunately, as technology progresses, these kinds of attacks are looking more and more official, increasing their victims. Another similar kind of attack is Password cracking. It is precisely as it sounds, attackers crack your password and access your information. They can do this through trial and error or programs that run any possible password into the system.
Computer systems are vulnerable to these attackers for a variety of reasons. A big reason is user error. By using weak passwords or clicking on sketchy emails, we end up allowing our systems to be attacked. A breach can cause a considerable amount of damage, including loss of information, trust, and business in many cases. People are not going to want to use a business that keeps losing their data. A way to avoid being breached is to be up to date with how attackers could access your system. By knowing what to watch out for, you are already ahead of the curve. Another is by having security systems that watch over your computer. There are a variety out there, and many that save people’s information daily. Attackers are out there, and it is crucial to take preventative measures to ensure your data security.
Post 4
After using tracert and ping, I think I have a better understanding of how packets travel through the network. Your computer sends a message through the network to the target network interface. The interface will then respond with a packet. You can first use ping to identify if the interface is available and able to send you packets. You can use tracert to see the path that the packet takes to get from your computer to the interface. As you can guess, the further away the interface is, the longer it will be to ping or trace it. If you are communicating with an oversea website, it might take longer than to use a local one. You can use ping to understand if the issue is your destination or your computer itself. If your computer is failing to receive the ping, it is your computer. If the website is failing to receive it, it is most likely the website. This could happen due to a multitude of reasons. One reason is security is blocking the ping for some reason. Another is that the route is blocked somewhere, and tracert will help you to see that.
Post 5
Operating systems –
Operating systems have always been an interest of
mine ever since I found out there was more than one. Finding out all the
different ones were mindblowing; I truly thought that it was all just one basic
system. Knowing what I know now, though, it makes sense how they differ, even
between phone operating systems like Apple or Android. The main question I
would have is, what truly makes one operating system unique from another? I
know that it has different commands and sometimes different buttons, but what
truly separates Linux and Windows, for example? What are the pros and cons of
both, and when would you prefer one over the other? Through my research, I plan
on watching videos and tutorials to use the different operating systems. I plan
to at least have a fundamental understanding between the different ones, and I
think that understanding only comes through use and practice.
Post 3
I have used Microsoft Word, Excel, and PowerPoint to complete my assignment. Each of these functions has benefits over each other, each useful in different scenarios. Microsoft Word is a word possessor, meaning it is best used in essays, speeches, or in creating significant words of text for multiple functions. You can change its design, but it struggles to present various images or statistics in a smooth and dynamic way. Microsoft Excel is a spreadsheet application that makes it easy to input numbers and statistics. You can easily create tables to show information, but you can also create databases within it. It struggles to show large amounts of text. Microsoft PowerPoint is a presentation function that creates a sort of middle ground between Word and Excel. It is easy to show text and statistics in a fun and engaging way. It struggles to show a lot of text, and it cannot create tables or databases.
After using all three, PowerPoint would be the most effective in documenting my day. It is able to hold all the information I was trying to convey while also allowing pictures and designs to exemplify what I was discussing. PowerPoint would also be useful in a work presentation when you are trying to teach someone else something. You do not overwhelm them with information like Word and Excel, and it allows you to engage your audience. Word would be best used in scholarly or educational articles. It is able to hold and show tons of text, making it most effective in these areas. Excel would be best used in calculating large amounts of statistical data and displaying them in cohesive charts. It is able to use functions and create databases, making it best at anything numbers.Post 2
Hello, a mobile app that I am familiar with is MacroFactor. MacroFactor is a tracking app created to assist you in tracking your calories and macronutrients. I have been using MacroFactor for a while, and it has made it easy to be able to know my daily intake. It was created by "Stronger by Science Technologies LLC," and I found it due to a youtube I watched, Jeff Nippard.
This app requires some work to operate correctly, mainly constant inputs of anything you consume in a day. You start off by answering some questions about yourself, your height, weight, activity level, experience, etc., and finish by setting a goal of weight loss, weight gain, or maintenance. It then calculates your general caloric intake for a day and also breaks it down further by giving you your macro goals(protein, fats, and carbohydrates). Initially, it seemed daunting to follow a stricter diet plan, but after starting, I found it much more freeing than I first thought. I found that I was actually eating way under my calorie goal and was not losing weight how I wanted because of it. Once I started eating more, I ended up losing more. It also does something really neat; it will adjust your intake values based on your weekly trends. Having an evolving meal plan is critical to being able to maintain any weight-changing journeys, lest they become monotonous and draining.
The design of the app is sleek and modern, with clear labels and explanations for any questions you may have. This is very helpful to anyone starting out because it can be intimidating going into something like this. It also has multiple charts and breakdowns of your eating trends, making it easy to monitor your weekly progress. On top of that, it has made inputting what I am eating easy and efficient. By scanning the barcode of anything I eat, finding it in a list of items, or describing it to an AI that finds what you are talking about, you will not have to struggle to input your consumption.
Even with how much I enjoy the app, there are still a few recommendations I would make. I will like to see a function that allows you to shift your goals easily. I am curious to see the caloric intake for more aggressive and passive weight loss plans, but it does not have a way of switching without starting all over. Another change would be a recent search button on the food inputs. Sometimes I will have a whole meal typed into the app and forget to hit the additional "Log Items" button, and it will cause me to have to start all over. Finally, I would like the ability to input how many calories I burn a day into it, not have it go off of estimates it assumes. Some days I will burn more calories than others, so it would be nice to have to shift goals to match that. But, even with these recommendations, I still would recommend this app to anyone who is trying to either gain, lose, or maintain their weight.
Nicholas Barnes CYB304 Final
Contemporary operating systems use a variety of features, such as memory management, I/O operations, error detection, accounting, program ...
-
Contemporary operating systems use a variety of features, such as memory management, I/O operations, error detection, accounting, program ...




