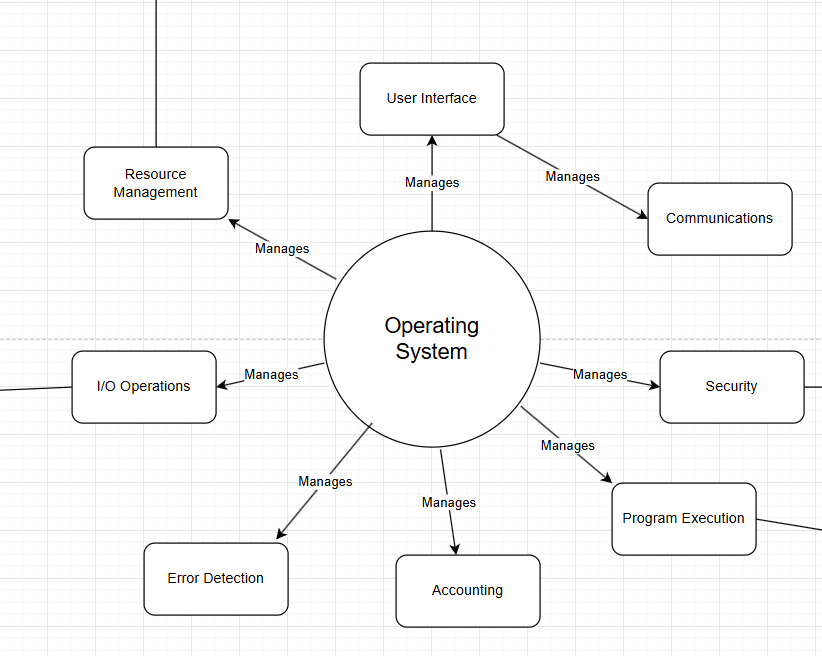
Contemporary operating systems use a variety of features, such as memory management, I/O operations, error detection, accounting, program execution, security, and user interface. This allows for a more complex but user-friendly system. It also allows for multitasking, something vital in the modern day-to-day. It can be represented in a multitude of ways, but I have chosen to show it in this way.
With the growing complexity of hardware and software, many operating systems may run into issues with memory management. Modern memory management is done through different memory storage, such as main memory and virtual memory. Main memory provides fast access to any stored data, while virtual memory allows the operating system to think it has more memory than actually exists. It becomes crucial to use the two together to effectively manage any memory in an operating system.
A few functions previously mentioned are the I/O operations, mass storage, and file management. Files are often organized using a separate system. This system specifically organizes, secures, and allows access to stored data. Mass storage is another form of storage within a device and provides the most storage space. Because of its size, it is also often the slowest form of storage. Finally, I/O devices describe how the user interacts with the system and how the system interacts back. A user would have to use an input device to send requests to the system, and the system uses output devices to respond.
These different concepts will not only help me in my day-to-day computer usage but will also allow me to gain insight into my future career. By knowing how security works and the role it plays within an operating system, I will be able to understand the core concepts of some of the issues I may run into. These core concepts provide a base from which my career in cyber security can be branched, and without them, I would be worse off than I would be with them.